AWS IAM - Essentials
Welcome to Cloud101
One of the biggest challenges of using cloud services is managing access to the resources. When your business-critical applications are running on cloud, it will be increasingly important to control the access to those resources to avoid losing your business. It is essentials that your team needs to have access to those resources while restricting the bad actors posing as legitimate users who are trying to access your resources with bad intentions.
Identity and Access Management service of AWS is one of the key services in adopting the AWS for your business. If you start using AWS without planning the IAM, you will end up dealing with 100s of users with 1000s of Roles and and Policy definitions that can be out of control very easily.
Depending on the email/collaboration service your are using for your team, you can choose many options on providing access to cloud resources.
Key Concepts of IAM.
Users, Roles, Groups, Policies and Permissions.
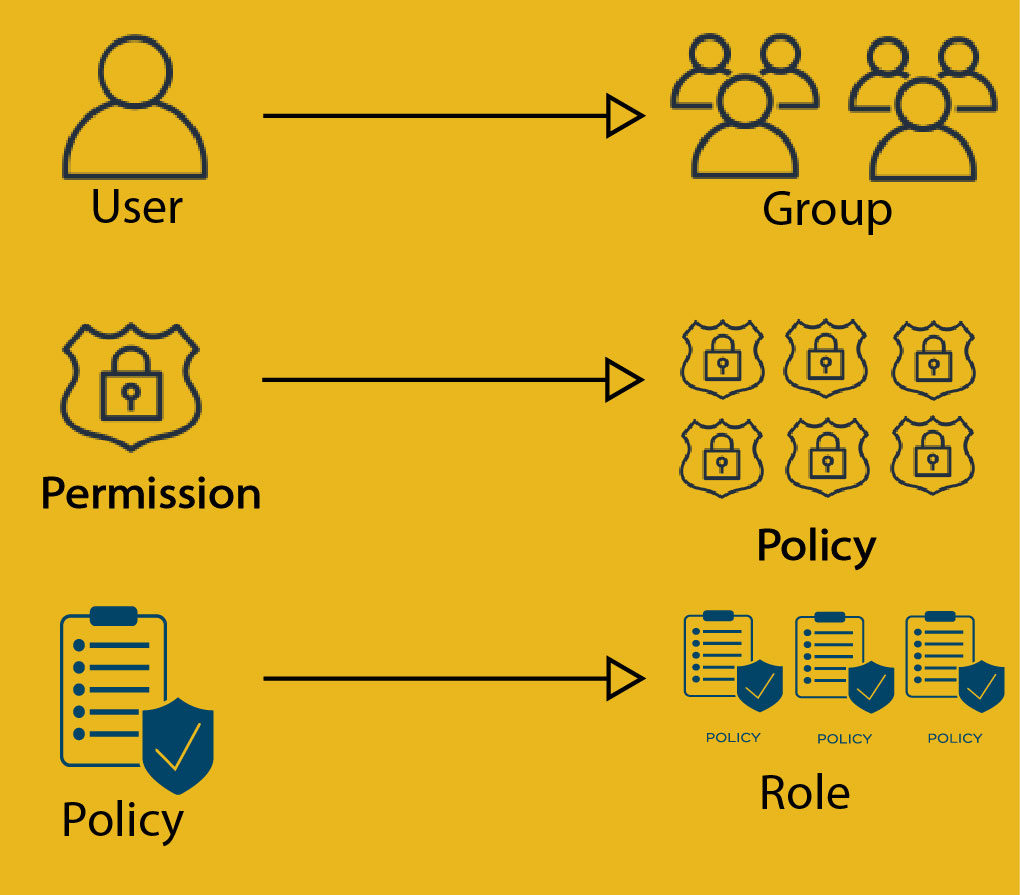
As you can see from the above picture, Permission is the lowest unit in IAM. When you combine multiple permissions, it becomes Policy. Similarly, when you combine multiple policies, it becomes a Role. At a glance, this seems pretty simple and straightforward, but in practice this can create lot of combinations and become complex and out of control.
Permission usually contains service and action you can provide on that service. Lets look at a sample Permission.
“iam:ListRoles”
In this case, we are dealing with the service “iam” and the action is “ListRoles”, so this permission allows a user to perform this action. When you combine this with other components like “Affect” and “Resource” you now have a policy. A policy can contain any number of permission, although it is advisable to have smallest number of permissions for a given policy to reduce security risks.
You can create any number of policies you want based on your requirement. Some policies are created by AWS itself in order to facilitate access among their services implicitly. Once you start creating policies, you will run into an use case where you are attaching more than one policy for a given user. This is when you must start using a Role to combine multiple policies.
Roles are the high-level abstraction on your policies to create more reusable permissions and speed up the access management process.
Finally, users and groups can help you manage users and put multiple users into groups to have more control access for a team of users. For example, your devops team needs to have different access from your dev team, so the easiest, way would be to create 2 groups, namely, DevOps and Dev and attach roles to them.
After this step, it would be easy to put team members in these groups based on their designation. If someone needs to have access to both of them, he can be a part both groups in order to get access to both resources.
Other interesting things in IAM.
ABAC (Attribute-based Access Control) makes it easy to provide access to resources based on tags. This is a very powerful feature.
AWS RAM (Resource Access Manager)
AWS AD services. There are various ways to connect your AD to provide access to users without login.
Conclusion
Overall, IAM allows you efficiently manage the access to your team in your organization. It is absolutely important to plan it properly before you start migrating to AWS Cloud.
I will be taking a DeepDive into AWS IAM in the videos section. So, keep an eye on it.
Thanks for reading.
